North Korea Targeted £850m In Four Year Hacking Spree

North Korea’s financial hacking operations are using increasingly sophisticated techniques as the country grows more desperate for cash, finds a new study
North Korea has attempted to steal more than $1.1 billion (£850m) over the past four years as a result of growing political and economic pressure, a new report has estimated.
The country’s attacks on banks and financial institutions date back at least to 2014, following the imposition of new UN sanctions, security group FireEye said.
The year is remembered for a damaging hack carried out against Sony Pictures, which was also attributed to North Korea.
But FireEye said North Korea’s state-backed hacking infrastructure is complex, with specialised operations for espionage and political purposes that are distinct from those aimed at bringing funds into the cash-strapped country.
Bank heists worldwide
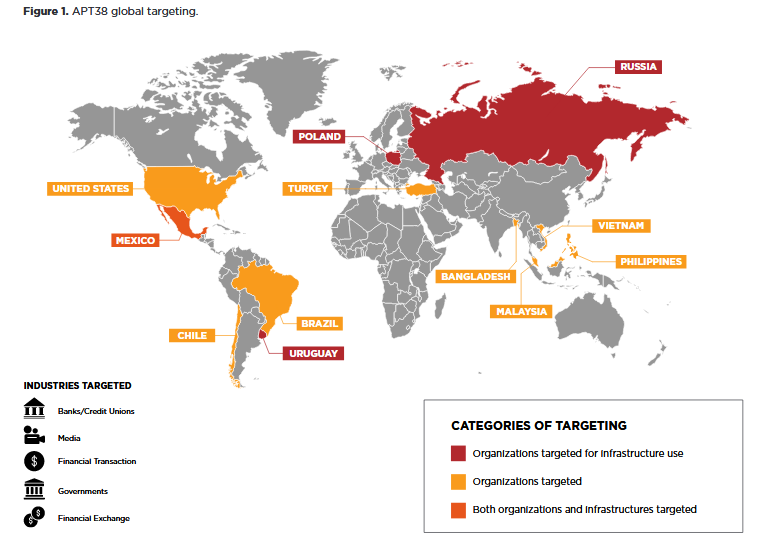
FireEye said enough is now known about North Korea’s financial hacking operations to give them a distinct designation. It refers to the country’s financial hacks with the term Advanced Persistent Threat 38 (APT38).
APT38’s operations are significant in themselves, having targeted more than 16 organisations in at least 11 countries since 2014, FireEye said in a new study.
North Korea has carried out its bank heists using techniques more commonly associated with espionage, including long periods of months or years in which the target is observed and infiltrated.
“Since the first observed activity, the group’s operations have become increasingly complex and destructive,” FireEye wrote. “APT38 has adopted a calculated approach, allowing them to sharpen their tactics, techniques, and procedures over time while evading detection.”
The firm said APT38’s operatives typically take an average of several months to examine a network after compromising it.
“On average, we have observed APT38 remain within a victim network approximately 155 days, with the longest time within a compromised system believed to be 678 days,” FireEye wrote.
APT38’s heists have included well-known incidents involving Bangladesh’s central bank, an attempted heist at Mexico’s Bancomext and a successful theft at Banco de Chile, the latter two during the course of this year alone.
New tactics
Of the $1.1bn targeted in these well-known operations, FireEye estimated the hackers made off with roughly $100m.
Its tactics have included deploying ransomware to destroy evidence, as it did following heists at Far Eastern International Bank (FEIB) in Taiwan, Bancomext and Banco de Chile.
FireEye said North Korea’s success at infiltrating banks and making fraudulent transfers using the SWIFT network has prompted increased security measures, which could lead APT38 to begin employing “new tactics”.
“The number of SWIFT heists that have been ultimately thwarted in recent years coupled with growing awareness for security around the financial messaging system could drive APT38 to employ new tactics to obtain funds, especially if North Korea’s access to currency continues to deteriorate,” FireEye wrote in the report.