Stealthy CosmicStrand Rootkit Infects PC Firmware

CosmicStrand rootkit found in UEFI firmware of computer systems of private individuals has evaded detection since end of 2016, say Kaspersky researchers
Security researchers have uncovered a stealthy rootkit that infects computers’ firmware and has been in use, undetected, since as far back as the end of 2016.
The CosmicStrand rootkit was uncovered in computers’ UEFI (Unified Extensible Firmware Interface), a software interface that resides on a chip separate from the rest of the system and links the operating system and the platform firmware, according to Moscow-based security firm Kaspersky Lab.
As such it can remain on the computer for the life of the system, no matter how many times the operating system is rebooted, and is highly difficult to detect.
Firmware compromise
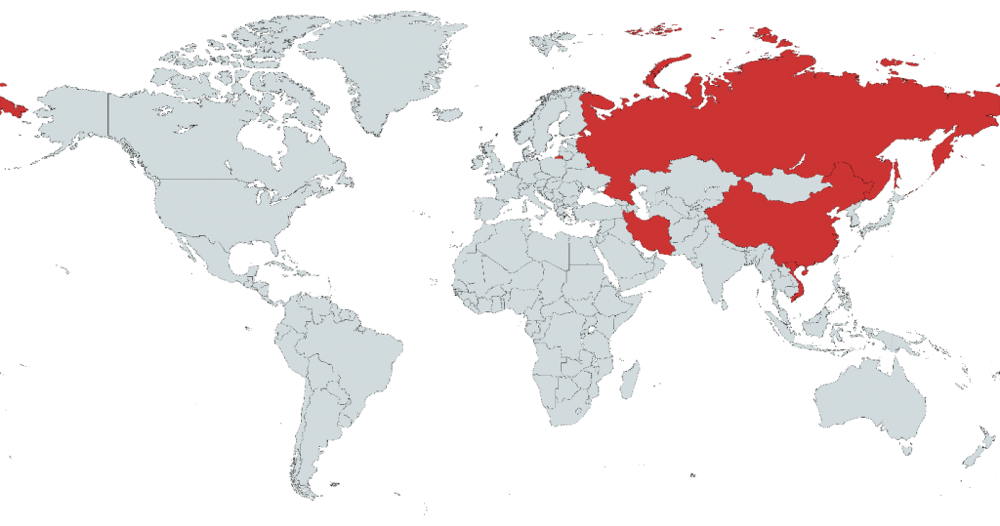
CosmicStrand has been mainly used to attack private individuals in China – as distinct from organisations – as well as a few attacks in Vietnam, Iran and Russia.
“All the victims in our user base appear to be private individuals,” Kaspersky said in an advisory. “We were unable to tie them to any organisation or even industry vertical.”
Kaspersky said it was unable to discover how the attackers infected systems initially, but it said unconfirmed reports sugested users had received compromised devices when ordering hardware components online.
“The rootkit is located in the firmware images of Gigabyte or ASUS motherboards, and we noticed that all these images are related to designs using the H81 chipset,” the firm said.
Common vulnerability
“This suggests that a common vulnerability may exist that allowed the attackers to inject their rootkit into the firmware’s image.”
Many details about CosmicStrand remain unknown, including its ultimate purpose.
Kaspersky said the CosmicStrand file within the UEFI, a mere 96.84KB, initiates a sequence that modifies Windows during boot and eventually downloads further code from a command server.
It said more implants and command servers could have remained undetected until now, while the last-stage payloads being delivered to targets also remains unknown.
China-based attackers
CosmicStrand is the second UEFI rootkit strain to be discovered this year after MoonBounce in January, which researchers believe was deployed as part of a targeted espionage campaign by the China-linked advanced persistent threat group APT41, also known as Winnti.
“The multiple rootkits discovered so far evidence a blind spot in our industry that needs to be addressed sooner rather than later,” Kaspersky said.
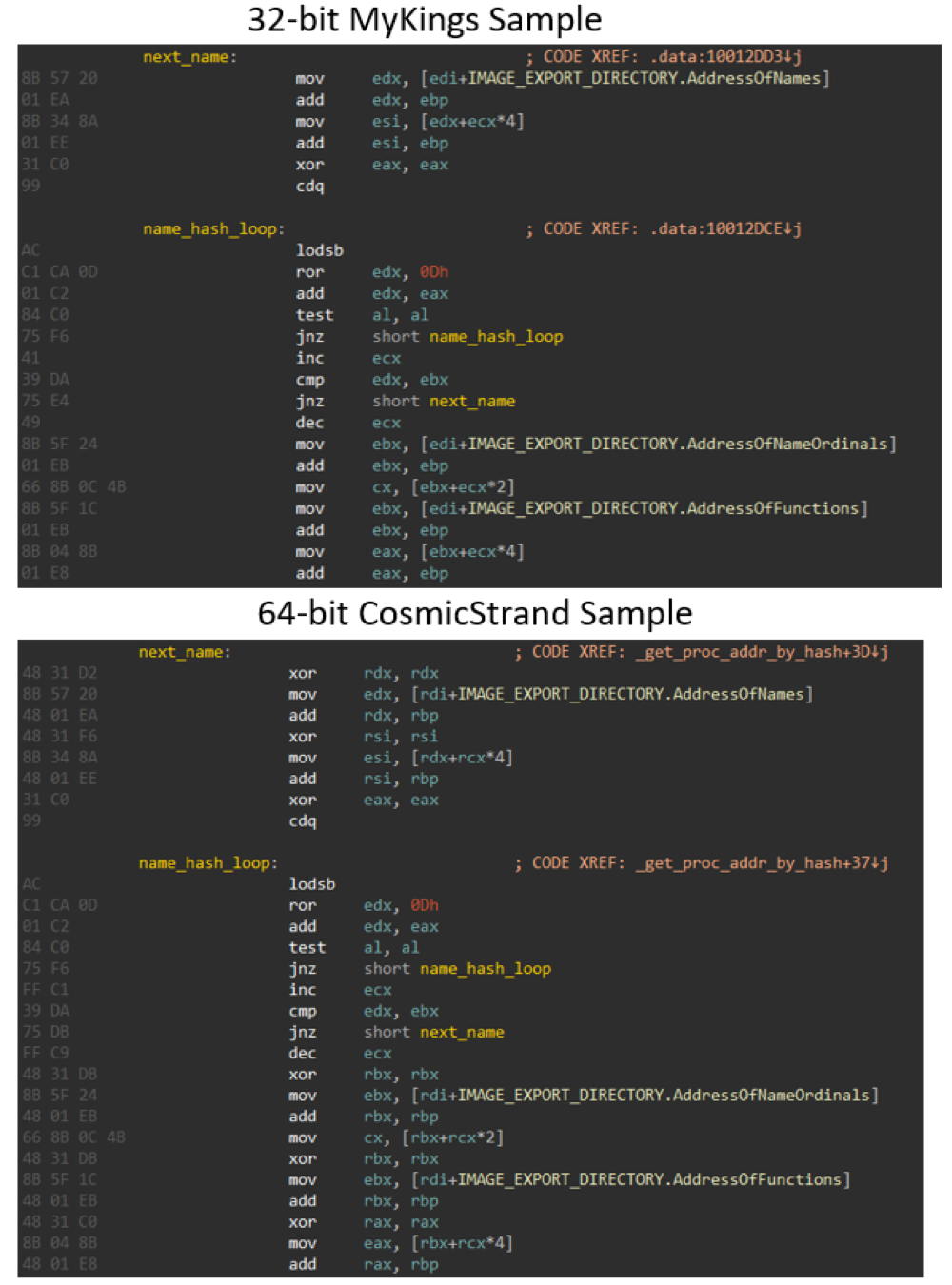
The firm said code overlaps between CosmicStrand, MoonBounce and the MyKings botnet indicate CosmicStrand could, like the other two malware strains, have been developed by Chinese-speaking attackers.
Sophistication
It noted that versions of CosmicStrand appear to have been in use since the end of 2016, long before UEFI attacks were first publicly described, emphasising the malware’s sophistication.
Kaspersky advised users to deploy security software and regularly update UEFI firmware.