Coinhive Cryptocurrency Mining Scripts Placed On Popular Sites

The Coinhive script introduced last month has quickly been adopted by hackers, who have maliciously placed it on legitimate sites
A script for mining cryptocurrency has been maliciously placed on popular sites across the web, according to researchers.
The Coinhive script can be placed on any web page and makes use of the processing power of computers viewing the site to carry out the mathematical operations used to ‘mine’ the currency Monero.
Malicious scripts
Those operating the script are awarded new coins upon completing the processor-heavy calculations, no matter whose computer systems carried out the actual processing tasks. The script’s developers market it as an alternative to conventional banner advertising.
But since the script was introduced on 14 September it has become lucrative business for hackers to place it wherever it’s likely to be viewed by large numbers of web users, even if for only a few seconds, according to Trend.
“Cybercriminal cryptocurrency mining is gaining traction because it’s an apparent non-zero-sum game,” wrote Trend fraud researcher Joseph Chen in an advisory. “Bad guys can profit even if they don’t invest much on creating their own malware — they can just misuse existing grayware.”
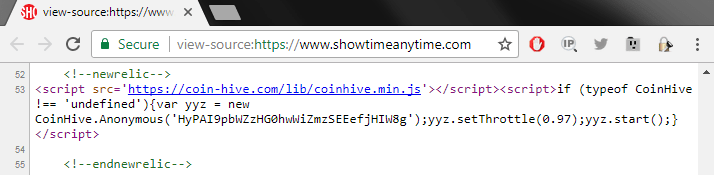
Coinhive has recently been detected on popular websites including the flagship site of CBS’ Showtime television network, showtime.com.
The script was found to use up to 60 percent of processor resources while running Coinhive on Showtime.com, according to an alert by researcher Troy Mursch.
Hidden placement
A promotional website operated by AirAsia, BIG Prepaid.com, and tuneprotect.com, used by leisure conglomerate Tune Group to sell travel insurance, were also found to contain Coinhive.
The code, which in both cases was concealed and encrypted, was quickly removed from both sites, with Tune Group confirming its placement had been “unauthorised”.
A scan of the most popular million websites found “hundreds” that contained Coinhive, including those of schools and charities, according to a report by the BBC.
The way the code was hidden on the sites indicated it was illicit, and the UK sites contacted by the BBC said they weren’t aware Coinhive was present.
Coinhive’s developers said they urge users to report unauthorised placement of the script and advise sites to inform users when the script is present. But doing so is left to the sites’ discretion.
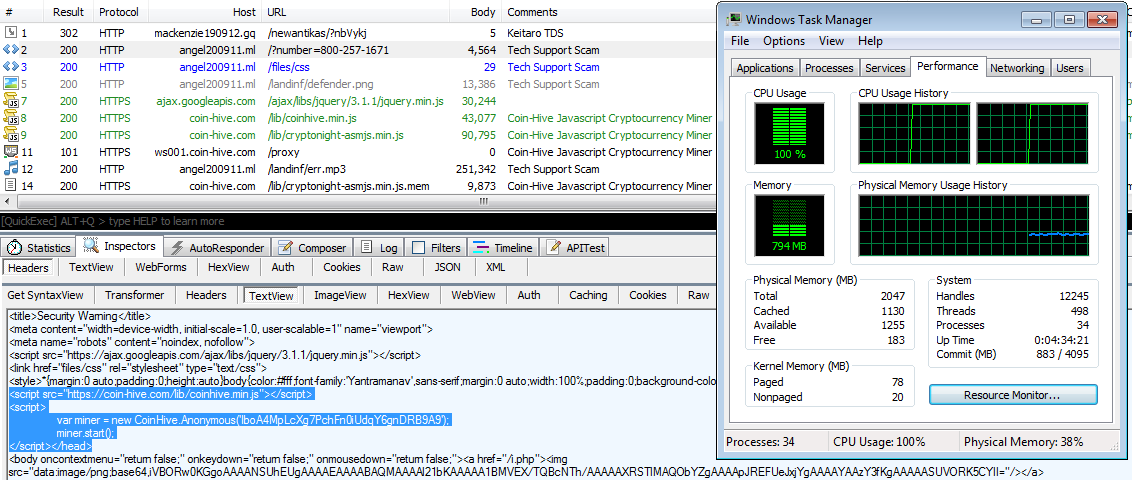
As a result, visitors to sites running Coinhive can experience system slowdowns as the page they’re viewing eats up system resources, researchers say.
File-sharing site The Pirate Bay attracted the ire of users when it quietly installed Coinhive last month. The site removed the script after users complained of the processor resources it used, and later said the move had been an experiment.
“This is only a test,” the site’s operators wrote. “We really want to get rid of all the ads. But we also need enough money to keep the site running.”
Developers embedded Coinhive into a popular Chrome extension called SafeBrowse and it has also been spotted on typosquatted domans, such as twitter.com.com.
Script ‘considered malicious’
Trend said some hackers have begun inserting Coinhive into their other scams as a way to earn extra funds. For instance, its study found the script inserted into a technical support scam page maliciously inserted into nearly 1,000 legitimate websites.
Between 1 January and 24 June of this year, Trend’s scanners found that 20 percent of the websites containing cryptocurrency mining scripts also contained web- and network-based attacks.
Because of its illicit use a number of security products now block script-based currency mining traffic.
Web traffic management firm Cloudflare has also terminated the accounts of some customers found to be using mining scripts without informing users.
Cloudflare said in a statement sent to those affected that it considered the script to be malicous if users weren’t notified of its presence.
“We consider this to be malware, and as such the account was suspended, and all domains removed from Cloudflare,” Cloudflare head of trust and safety Justin Paine said in the message.
Several firms offering cloud-based computing power have also reported issues with hackers misusing customers’ accounts to mine cryptocurrencies, the BBC said in its report, citing University of Illinois computer scientist Matthew Caesar.
Caesar, who is developing a monitoring tool to detect illicit mining activity, said those affected can be presented with huge bills run up by hackers.
Do you know all about security in 2017? Try our quiz!