Popular Barcode Scanner App Transforms Into Adware

Malwarebytes issues warning, after update to a popular barcode scanning app on Google Play, transforms it into adware pusher
Google has reacted quickly and removed a popular Android app on its Google Play Store, that was discovered to the source of unwanted advertising.
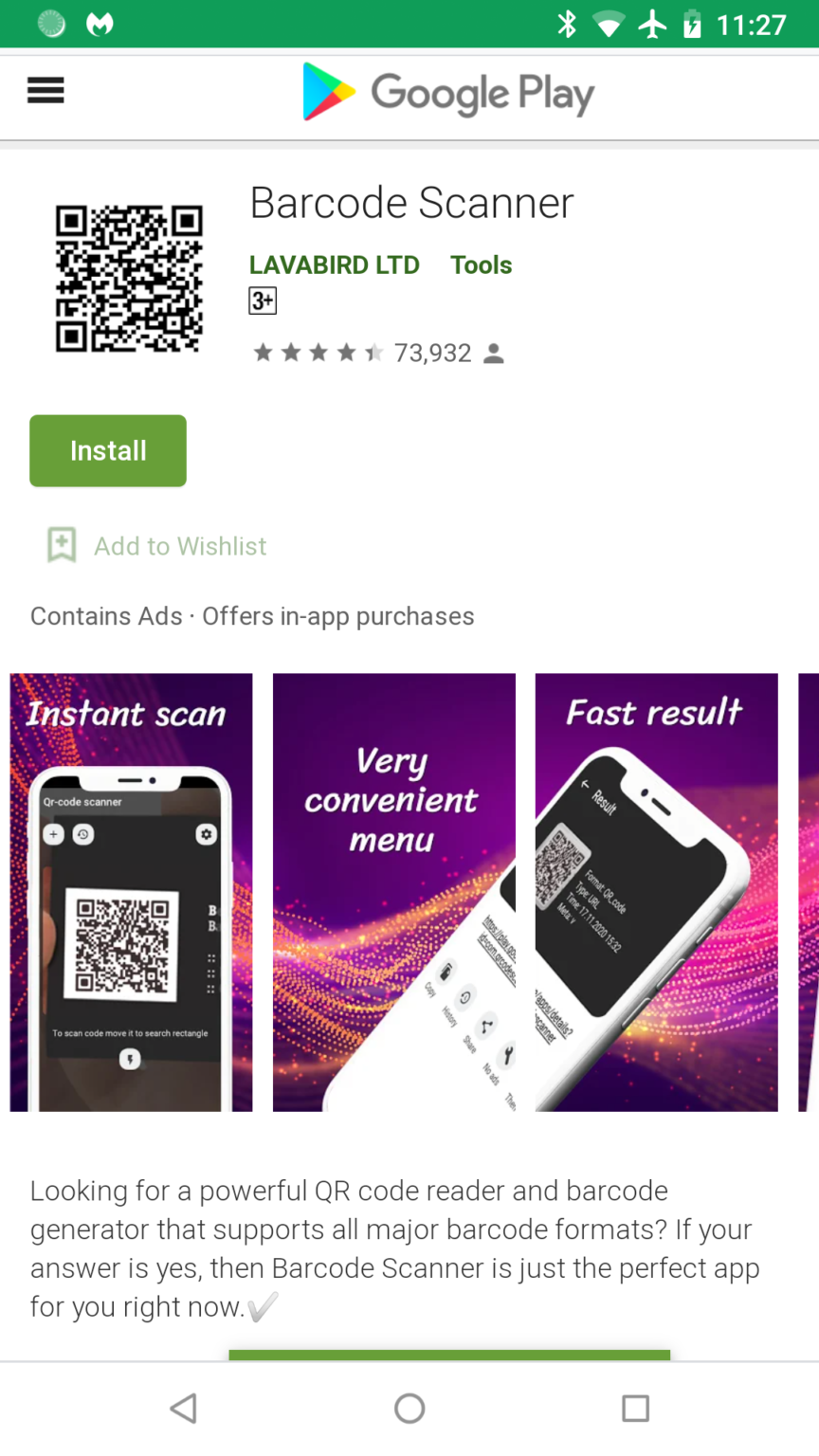
The rogue app in question is called Barcode Scanner, and Malwarebytes explained in a blog post last week how its forum users had tipped off its security researchers about the app.
What makes this an issue is that Barcode Scanner had been downloaded 10 million times, but “after an update in December, Barcode Scanner had gone from an innocent scanner to full on malware!” said Malwarebytes.
Adware infection
“Late last December we started getting a distress call from our forum patrons,” the security researchers blogged. “Patrons were experiencing ads that were opening via their default browser out of nowhere. The odd part is none of them had recently installed any apps, and the apps they had installed came from the Google Play store.”
“Then one patron, who goes by username Anon00, discovered that it was coming from a long-time installed app, Barcode Scanner,” Malwarebytes wrote. “An app that has 10,000,000+ installs from Google Play! We quickly added the detection, and Google quickly removed the app from its store.”
The Barcode Scanner is from a company called LavaBird Ltd, which reportedly has at least four other apps on the Google Play Store.
The firm reportedly uses an address in central London, which is reported to be just a forwarding service as other companies are also registered at the same address.
LavaBird, according to the Register, seems to have been registered in London in March 2020 by a 23-year-old Ukrainian man who lives in Kyiv.
And Malwarebytes has alleged that the LavaBird deliberately hide the change in code in the update.
“The majority of free apps on Google Play include some kind of in-app advertising,” blogged Mlawarebytes. “They do this by including an ad SDK to the code of the app. Usually at the end of the app’s development. Paid-for versions simply do not have this SDK included.”
Malign intent
“But every once in a while, an ad SDK company can change something on their end and ads can start getting a bit aggressive,” said the security firm. “Sometimes even landing the apps that use it in the Adware category. When this happens, it is not the app developers’ doing, but the SDK company. I explain this method to say that in the case of Barcode Scanner, this was not the case.”
“No, in the case of Barcode Scanner, malicious code had been added that was not in previous versions of the app,” Malwarebytes blogged. “Furthermore, the added code used heavy obfuscation to avoid detection. To verify this is from the same app developer, we confirmed it had been signed by the same digital certificate as previous clean versions. Because of its malign intent, we jumped past our original detection category of Adware straight to Trojan, with the detection of Android/Trojan.HiddenAds.AdQR.”
“It is hard to tell just how long Barcode Scanner had been in the Google Play store as a legitimate app before it became malicious,” said Malwarebytes. “Based on the high number of installs and user feedback, we suspect it had been there for years.”
“It is frightening that with one update an app can turn malicious while going under the radar of Google Play Protect,” it concluded. “It is baffling to me that an app developer with a popular app would turn it into malware. Was this the scheme all along, to have an app lie dormant, waiting to strike after it reaches popularity? I guess we will never know.”
Users are advised to uninstall the app, and Malwarebytes provided the hyperlink of the offending app (available here), to avoid confusion as there are plenty of genuine barcode scanner apps still on Google Play.