US Government Shutdown Disrupts Security On .Gov Sites

Researchers find dozens of expired security certificates affecting sensitive sites used by the likes of NASA and the Department of Justice, blocking some services and exposing others to attack
Researchers have found dozens of expired security certificates on US government websites, many affecting sensitive services.
The expired certificates, which security firm Netcraft said had probably not been renewed due to the ongoing partial US government shutdown, make some services difficult to access, while in other cases they may expose users to risks.
The sites affected include government payment portals and remote access services used by organisations including NASA, the Department of Justice and the Court of Appeals.
The shutdown, the longest in US history, occurred due to conflict over approving the government’s budget. It has affected around 800,000 federal staff, with roughly half of those having been placed on furlough.
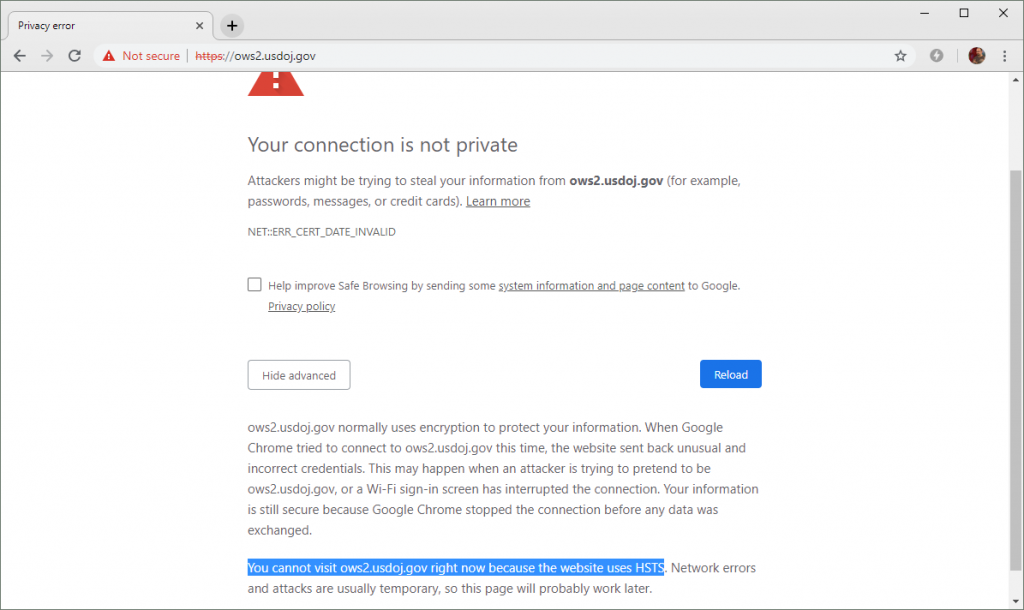
Sites blocked
Netcraft found that more than 80 TLS certificates used by .gov websites had expired and had not been renewed, with some of the sites being made all but inaccessible due to the expiration.
One site used by the Department of Justice, for instance, uses a certificate that expired on 17 December of last year, is inaccessible due to its use of a strict policy that bars most browsers from loading the page if the certificate has expired.
The policy, called HSTS preloading, means that if a site’s certificate has expired, users see an error message when they try to access the site.
The error message can be bypassed using advanced settings, but those are deliberately made difficult to spot, Netcraft said.
“While this behaviour is bound to frustrate some users, in this case, security is arguably better than usability,” said Netcraft’s Paul Mutton in an advisory.
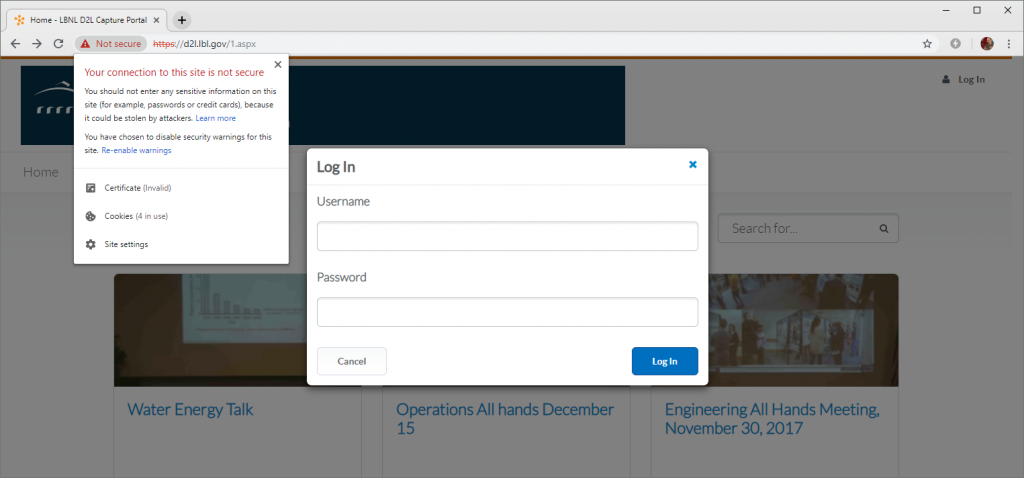
Insecure login
Other US government sites lack correctly functioning HSTS policies and instead only display an interstitial warning that can easily be bypassed, Mutton said.
Those sites may present security concerns, since many users are likely to access them without a working security certificate.
That can expose them to risks such as man-in-the-middle attacks, Mutton said. Such attacks effectively allow an attacker to eavesdrop on the user’s communication with a site, potentially stealing sensitive data such as login credentials.
Netcraft found that one Berkeley Lab government website, for instance, presented a login form with an expired certificate.
“As there is no effective HSTS policy, users can ignore the browser’s warnings and proceed to the login form,” Mutton wrote.
He said the government shutdown is likely to mean more ongoing security risks.
“As more and more certificates used by government websites inevitably expire over the following days, weeks — or maybe even months — there could be some realistic opportunities to undermine the security of all U.S. citizens,” Mutton wrote.