Rootkit Malware Hijacks Systems To Drive Advertising Traffic

Scranos first appeared last November, but has already spread to tens of thousands of systems around the world
A rootkit-driven malware strain that first appeared only late last year has already spread to tens of thousands of systems worldwide, researchers say, as its creators use it to drive false traffic for web-based advertising.
Bitdefender said it began analysing the malware that it calls Scranos last year, finding that while it already has a high degree of sophistication it is also being actively developed, with its developers using infected systems to test new components and update older ones.
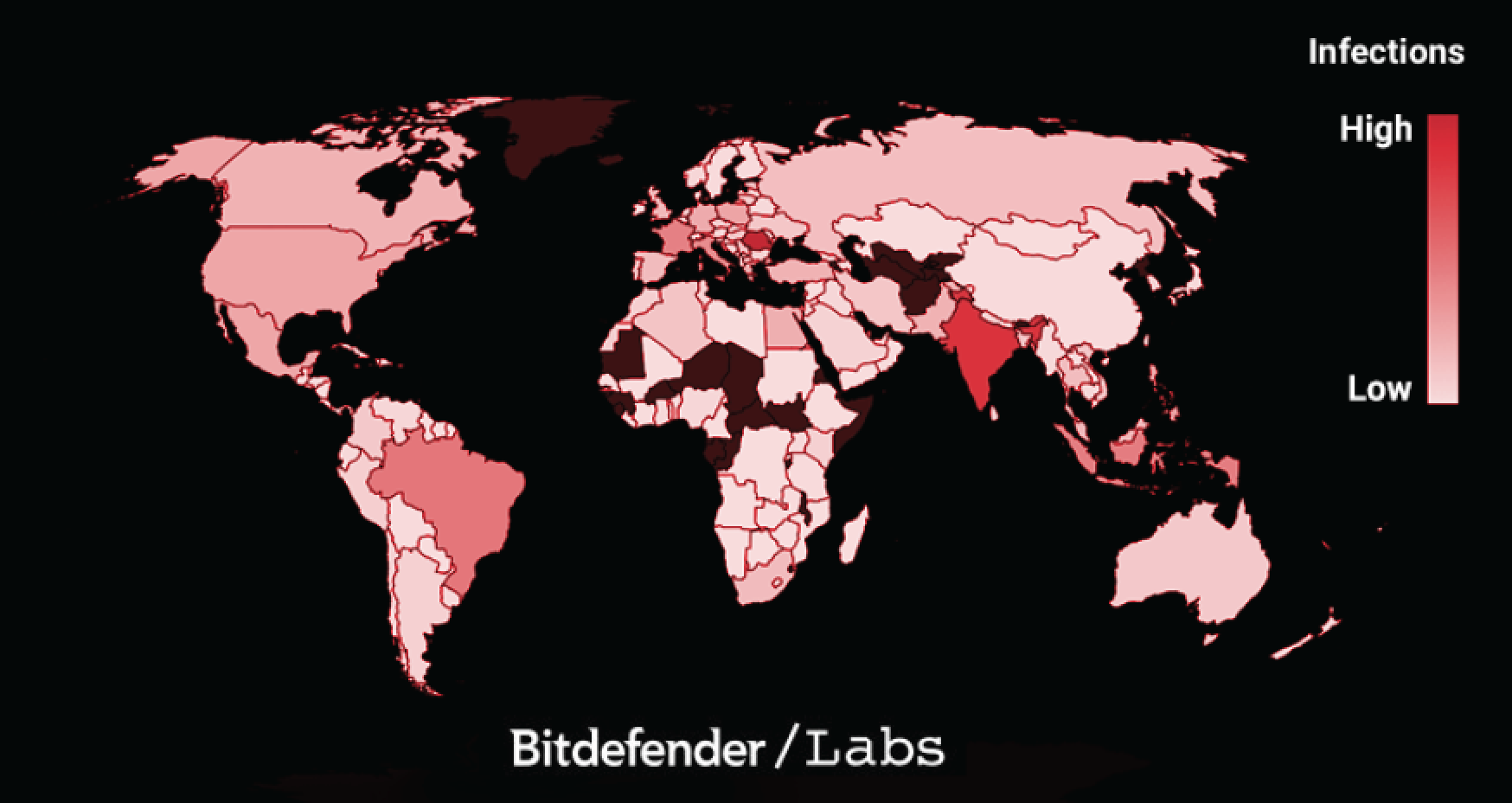
Scranos began by infecting systems in China, as Tencent warned in January, but is now found on systems worldwide, with France and Italy amongst its top international targets, as well as India, Romania, Brazil and Indonesia.
Researchers said the botnet’s control servers have recently begun distributing other malware to infected computers, indicating Scranos’ controllers are likely to have become involved in a pay-per-install scheme.
Hidden in software
The malware initially infects systems via a Trojanised application that may appear to be cracked software or a legitimate utility such as a video player or an e-book reader.
It is signed with a legitimate security certificate, probably stolen, that was issued to a Shanghai-based health company. The certificate hasn’t been revoked in spite of the misuse, Bitdefender said.
Scranos installs a rootkit that allows it to remain persistent on Windows systems, and is capable of downloading and installing other components that carry out a wide range of tasks.
However, the malware appears to be mainly focused on driving fraudulent advertising traffic, particularly to YouTube
It opens a hidden window using the Chrome browser and plays muted YouTube videos, as well as subscribing the user to particular YouTube channels. In one case, Bitdefender found that the malware added more than 3,100 subscribers to a particular channel in a single day.
If Chrome isn’t found on a system, Scranos is capable of installing it.
Facebook phishing
The malware attempts to hide any traces of its activities, deleting all payloads after they’ve served their purpose.
Scranos can also extract cookies and steal login credentials from a range of browsers, misuse payment accounts on Facebook, Amazon and Airbnb, send friend requests to other accounts from a user’s Facebook account, and send phishing messages containing malicious APKs to a user’s Facebook friends, amongst other capabilities.
Scranos first appeared in November 2018, and distribution spiked in December and January, with most infections currently on Windows 10 computers.
While infections have levelled off for the moment, Bitdefender said Scranos’ authors are working aggressively to update the malware.
“Despite the sophistication, this attack looks like a work in progress, with many components in the early stage of development,” Bitdefender said in its advisory.
“The operators of this rootkit-enabled spyware are continuously testing new components on already-infected users and regularly making minor improvement to old components… Although the campaign has not reached the magnitude of the Zacinlo adware campaign, it is already infecting users worldwide.”