Kaspersky
Lab researchers have uncovered a technically sophisticated
cyberespionage framework, TajMahal,
which has been active since at least 2013 and appears to be unconnected
to any known threat actors. It features around 80 malicious modules and
includes functionality never before seen in an advanced persistent
threat (APT), such as the ability to steal information from printer
queues and grab previously seen files from a USB device.
This press release features multimedia. View the full release here:
https://www.businesswire.com/news/home/20190410005147/en/
The TajMahal cyberespionage platform is a previously unknown, advanced APT framework that has been active since at least 2013. (Graphic: Business Wire)
Kaspersky Lab researchers discovered TajMahal in late 2018. It is a
technically sophisticated APT framework designed for extensive
cyberespionage. Malware analysis shows that the platform has been
developed and used for at least the last five years, with the earliest
sample dated April 2013, and the most recent August 2018. The name
TajMahal comes from the name of the file used to exfiltrate the stolen
data.
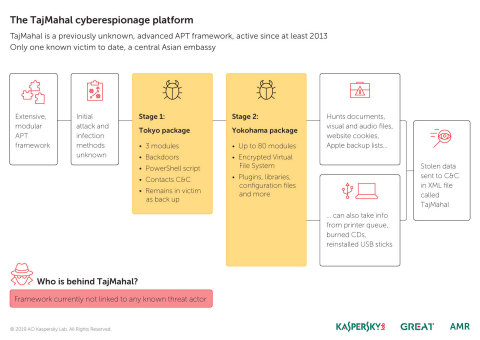
The TajMahal framework is believed to include two main packages,
self-named as ‘Tokyo’ and ‘Yokohama.’
Tokyo is the smaller of the two, with around three modules. It contains
the main backdoor functionality, and periodically connects with the
command and control servers. Tokyo leverages PowerShell and remains in
the network even after the intrusion has moved to stage two.
Stage two is the Yokohama package: a fully armed spying framework.
Yokohama includes a Virtual File System (VFS) with all plugins, open
source and proprietary third-party libraries, and configuration files.
There are nearly 80 modules in all, and they include loaders,
orchestrators, command and control communicators, audio recorders,
keyloggers, screen and webcam grabbers, documents and cryptography key
stealers.
TajMahal is also able to grab browser cookies, gather the backup list
for Apple mobile devices, and steal data from a CD burnt by a victim as
well as documents in a printer queue. It can also request the theft of a
particular file from a previously seen USB stick, and the file will be
stolen the next time the USB is connected to the computer.
The targeted systems found by Kaspersky Lab were infected with both
Tokyo and Yokohama. This suggests that Tokyo was used as first stage
infection, deploying the fully-functional Yokohama package on
interesting victims, and then left in for backup purposes.
So far, only one victim has been observed: a foreign based, central
Asian diplomatic entity, infected by 2014. The distribution and
infection vectors for TajMahal are currently unknown.
“The TajMahal framework is a very interesting and intriguing finding,”
said Alexey Shulmin, lead malware analyst at Kaspersky Lab. “The
technical sophistication is beyond doubt and it features functionality
we have not seen before in advanced threat actors. A number of questions
remain. For example, it seems highly unlikely that such a huge
investment would be undertaken for only one victim. This suggests that
there are either further victims not yet identified, or additional
versions of this malware in the wild, or possibly both. The distribution
and infection vectors for the threat also remain unknown. Somehow, it
has stayed under the radar for over five years. Whether this is due to
relative inactivity or something else is another intriguing question.
There are no attribution clues nor any links we can find to known threat
groups.”
In order to avoid falling victim to a targeted attack by a known or
unknown threat actor, Kaspersky Lab researchers recommend implementing
the following measures:
-
Use advanced security tools like Kaspersky
Anti Targeted Attack Platform (KATA) and make sure your security
team has access to the most recent cyber threat intelligence. -
Make sure to update all software used in your organization on a
regular basis, particularly whenever a new security patch is released.
Security products with Vulnerability Assessment and Patch Management
capabilities may help to automate these processes. -
Choose a proven security solution such as Kaspersky
Endpoint Security that is equipped with behavior-based detection
capabilities for effective protection against known and unknown
threats, including exploits. -
Ensure staff understand basic cybersecurity hygiene, as many targeted
attacks start with phishing or other social engineering techniques.
All Kaspersky Lab products successfully detect and block this threat.
A report on the TajMahal APT framework can be found on Securelist.
About Kaspersky Lab
Kaspersky Lab is a global cybersecurity
company, which has been operating in the market for over 21 years.
Kaspersky Lab’s deep threat intelligence and security expertise is
constantly transforming into next-generation security solutions and
services to protect businesses, critical infrastructure, governments and
consumers around the globe. The company’s comprehensive security
portfolio includes leading endpoint protection and a number of
specialized security solutions and services to fight sophisticated and
evolving digital threats. Over 400 million users are protected by
Kaspersky Lab technologies and we help 270,000 corporate clients protect
what matters most to them. Learn more at www.kaspersky.com
.
View source version on businesswire.com: https://www.businesswire.com/news/home/20190410005147/en/